The combined Synack/Tenable solution reduces alert noise for overloaded security teams, isolating the most exploitable threats so they can proactively close security gaps faster.
Vulnerability Assessment 🤝 Penetration Testing
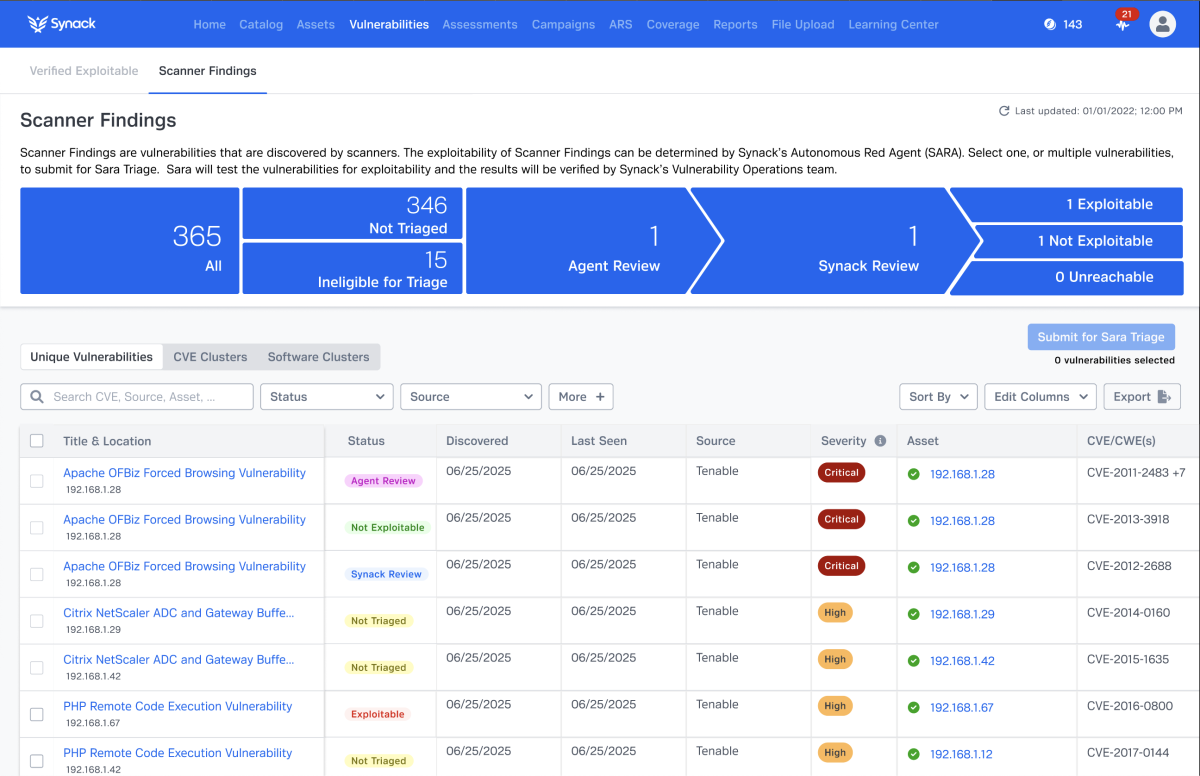
Vulnerability assessment, including automated scanning, is a great first step in identifying potential security risks. However, massive amounts of data can make it tricky for security teams to prioritize the exposures that real-world attackers are most likely to exploit.
Penetration testing complements vulnerability assessment by confirming exploitability while providing detailed analysis, paths to remediation and patch verification, so teams can proactively close security gaps before bad actors can exploit them. But penetration testing and vulnerability management have traditionally been siloed.
The solution: Synack, the leader in human-led and AI-powered Penetration Testing as a Service (PTaaS), has partnered with Tenable to offer the best of both worlds. Customers can get vital insights from Tenable Vulnerability Management integrated with Synack’s AI-assisted vulnerability triage and penetration testing. This all-in-one security partnership leverages the extensive vulnerability intelligence provided by Tenable Research and is backed up by the power of the Synack Red Team, a vetted group of 1,500 ethical hackers who ensure vulnerability results are actionable — and that your fixes actually work.
3 key takeaways: Solving cybersecurity challenges
Here’s a look at three real-world challenges facing security teams, how they benefit attackers and how the Synack + Tenable partnership can help:
Challenge: Automated scanning inundates security teams with alerts.
- Risk: Over
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.This article has been indexed from Security BoulevardRead the original article: