In an age where cyber threats continue to grow in
sophistication and
frequency, the pursuit of a unified threat contextualization platform is no
longer a mere convenience but an absolute necessity. When faced with an
unfamiliar file, hash, domain, IP address, or URL, having a singular view of
threat intelligence not only expedites investigations but also helps
eliminate detection blind spots.
sophistication and
frequency, the pursuit of a unified threat contextualization platform is no
longer a mere convenience but an absolute necessity. When faced with an
unfamiliar file, hash, domain, IP address, or URL, having a singular view of
threat intelligence not only expedites investigations but also helps
eliminate detection blind spots.
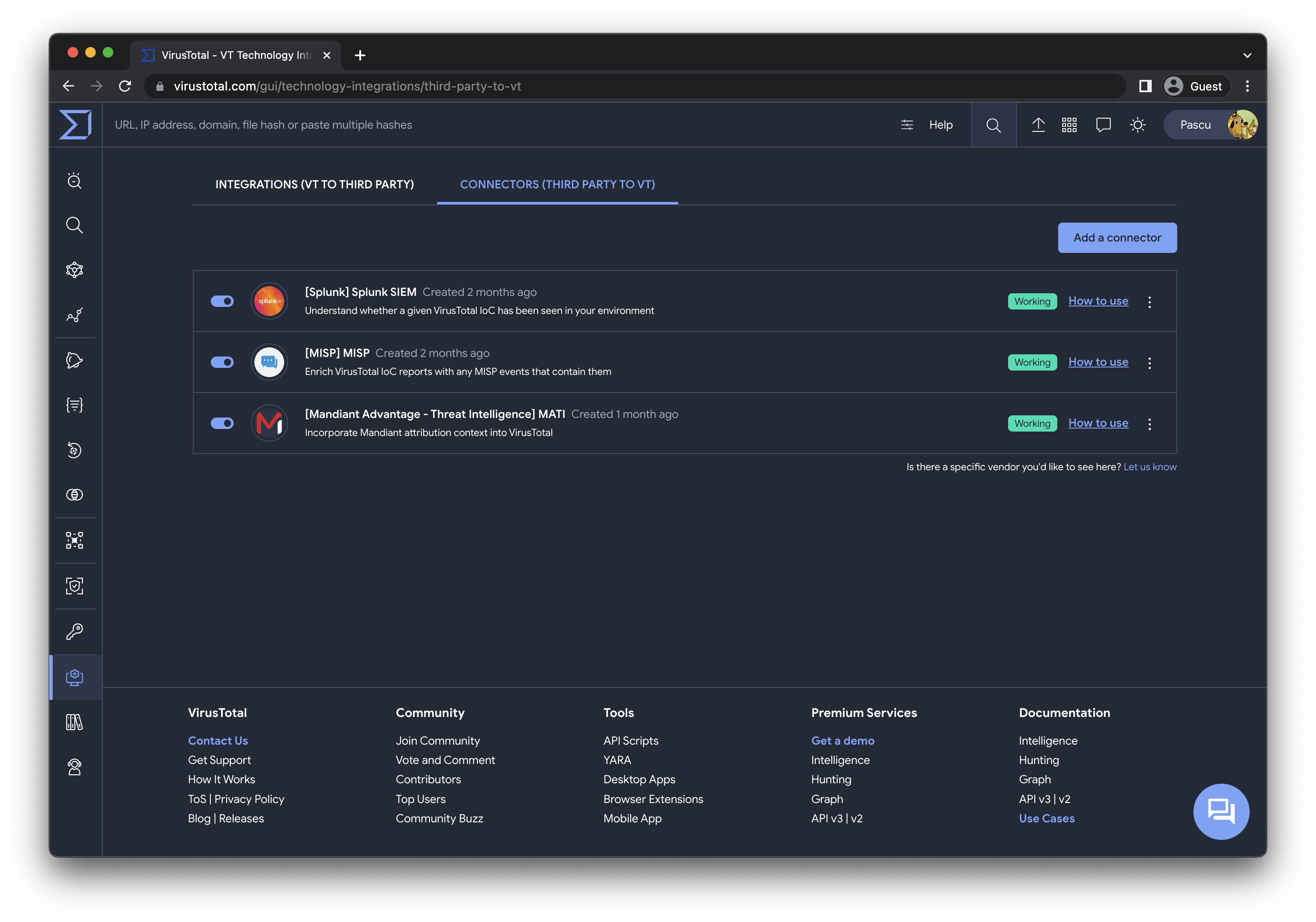
Today, we are taking a significant step toward realizing
this unified
threat contextualization with VirusTotal Connectors. That’s right. All your
Threat Intel intelligence from third parties will seamlessly be merged with
VirusTotal’s context!
this unified
threat contextualization with VirusTotal Connectors. That’s right. All your
Threat Intel intelligence from third parties will seamlessly be merged with
VirusTotal’s context!
Complementary threat context
<
div>
While this post doesn’t delve into specific third-party connectors,
we’re excited to announce that Mandiant is among our first supported
connectors. More details about this will be covered in an upcoming
blog post.
<p dir="ltr" style="font-size: 11pt; line-height: 1.38; margin-bottom: 0pt; margin-top: 0pt;">
<span style="font-size: 11pt; vertical-align: baseline;">In addition to Mandiant, we are introducing two other connector
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
This article has been indexed from VirusTotal Blog