A study conducted by Enterprise Strategy Group, now part of Omdia, in partnership with Tenable shows responsibility for exposure management scattered across multiple teams with conflicting priorities. It’s time to build the team of the future — discover what ‘good’ looks like and how to get there.
Key takeaways
- Teams are fragmented, with most organizations lacking a dedicated vulnerability or exposure management team.
- Conflicting priorities slow progress as IT and security teams often have different KPIs, causing delays.
- Success requires collaboration, bringing key security functions under one umbrella and fostering cooperation across teams, not just tools.
- Start small and build momentum by proving value with one team, unit, or use case before expanding.
- Leverage existing resources, using an exposure management platform to maximize your people and tools.
Do you know who owns threat and exposure management in your organization?
It’s not a trick question. The obvious answer that springs to mind would be, “the vulnerability or exposure management team, of course!”
Yet, a recent study conducted by Enterprise Strategy Group in partnership with Tenable shows that for most organizations the responsibility for threat and exposure management spans multiple teams — dominated by IT operations, cloud security and the security operations center (SOC). Only 41% of organizations say the vulnerability or exposure management team is responsible for managing threats and exposures
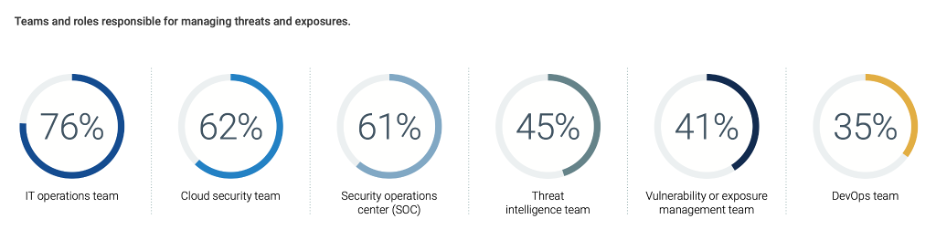
Source: Enterprise Strate
[…]
Content was cut in order to protect the source.Please visit the source for the rest of the article.
Read the original article: